Application Security 101
Most developers and companies believe their applications to be secure and understand the importance of security.
However year after year they continue to push vulnerable code into production.
In order to avoid these pitfalls and improve the overall security of our applications we need to understand what application security is all about.
What is Application Security?
The first thing to understand here is that by application we mean Web, Mobile and Enterprise Applications.
Application security means means the Software Building and Deploying are protected from dangers.
It involves taking necessary steps through out the project lifecycle to ensure and prevent malicious actors from accessing any part of your data, confidential or non-confidential.
Why is it important?
In simple terms, it is like placing smoke detectors throughout our code and different software to alert us about vulnerabilities found or issues in the code.
We need digital locks so that people who are pretending to be legitimate users do not gain access to our data, or worse destroy it!
Suppose your data servers are hacked and the hackers are demanding Bitcoins to giving the access back.
You wouldn't want that right??
Well, that is why creating a secure application is important.
6 Pillars of Application security
Although every app is different, and require different levels and types of security, these can be broadly classified into 6 different types of practices and methods :
Authentication and Authorization
Authentication is about identifying you within a system, that is you are a legitimate person and not someone or a system faking to be someone else.
Authorization is about how much access you have as a User, which basically means that scope of data visible to you.
A simple example would be an app like Whatsapp.
You create your account using your name and mobile number. To prove that you are actually a real user with a valid mobile number, you receive an OTP. This is Authentication
Now, when you are logged in, you can access your own message but you cannot access other users' messages. This is because You are NOT❌ Authorized to see their messages.
Since, authentication and authorization work together, they are referenced together.
Data Processing
Data processing can also be thought of as Input Handling. This basically means that when users are entering data into your system, they do so in a way that your expectations are met.
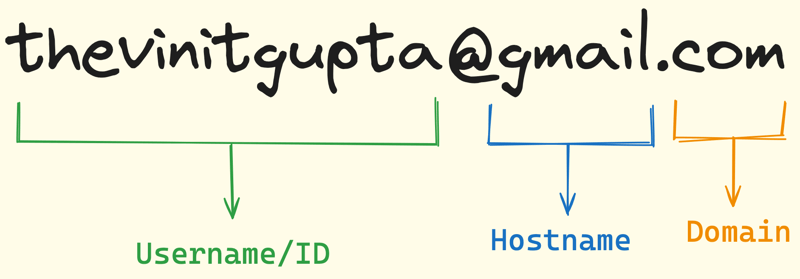
An example is when users are entering an email, it needs to be of the form :
You don't expect it to be something else like Code or a script that could potentially expose your data. This is called Cross Site Scripting or XSS attack.
You need to make sure that users are not able to do this in forms or in any other way.
You also need to make sure that this doesn't happen with data coming from other sources as well.
Encryption
Now, encryption can mean a lot of different things in different aspects.
In simple terms, and maybe I would be oversimplifying things a little bit here :
Encryption means hiding information and locking it in such a way that you cannot access it unless you have the right key.
Suppose your data has been breached somehow. If you would have stored the password after encryption, the hacker would not be able to fake someone's identity.
You would use an algorithm with a specific key to transform the data into a form which is not Human Readable 🕵🏻♂️.
Logging
Yes, I know. Most of you reading this would be saying :
"How logging errors and issues would make an application secure??"
You're right. It wouldn't.
Not directly.
Once an issue has been logged, it can be monitored and analyzed. And with the help of this, future breaches due to issues could be reduced.
Testing
Testing consists not just of ensuring that the functions and operations within your code are behaving as expected, but also to handle the unexpected scenarios too.
But that's just one area of testing.
Testing also includes : Security Testing
An example of security testing is Penetration Testing. It involves having security researchers and experts attempt to break into your applications periodically, to ensure that it is still safeguarded against these attacks.
This can be cumbersome sometimes if done manually, but necessary.